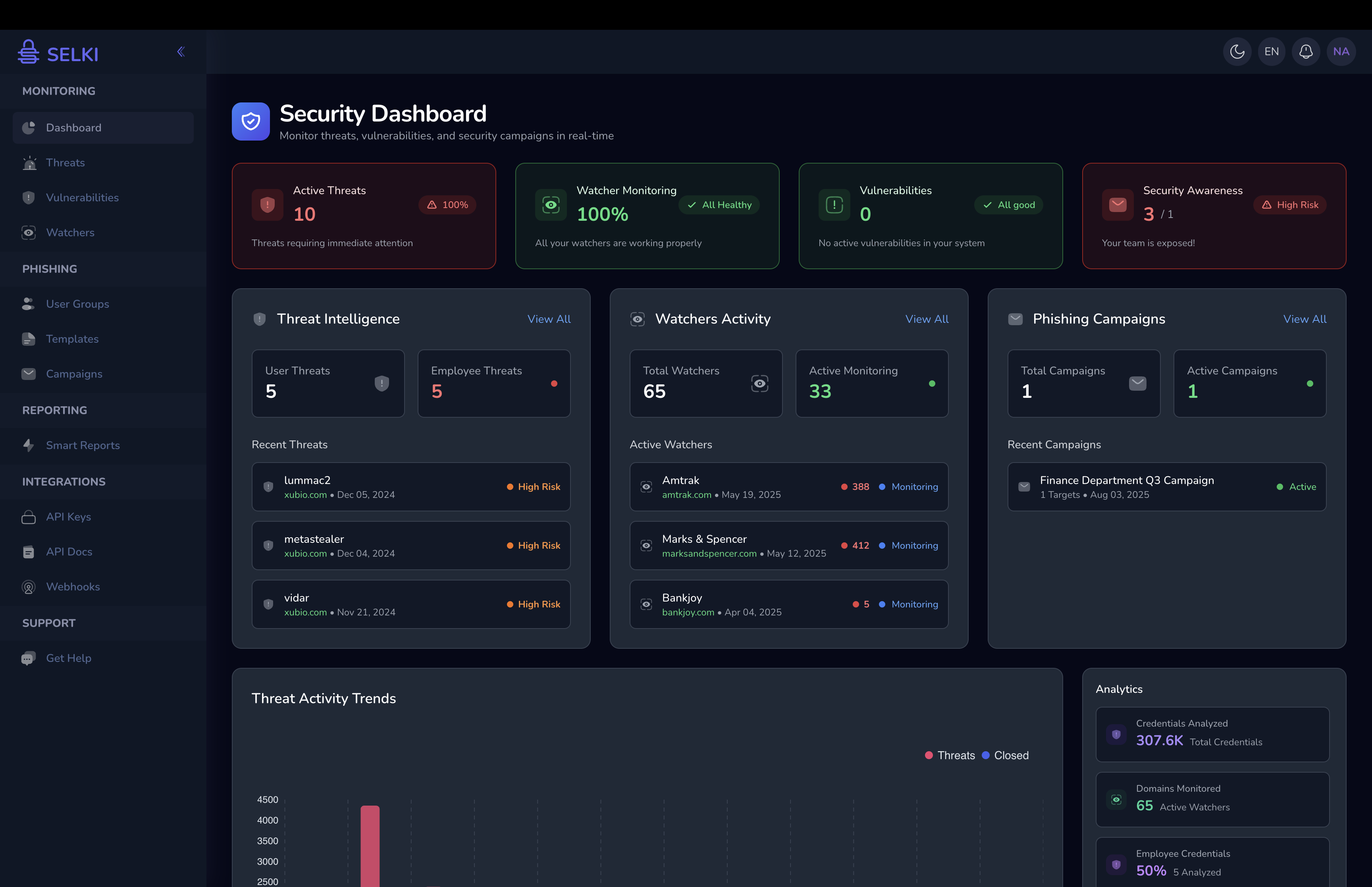
Transform your cybersecurity with a solution that identifies threats before they impact your business, assesses risk with precision, and shields your most valuable assets. An intelligent defense that adapts and evolves with every new threat.
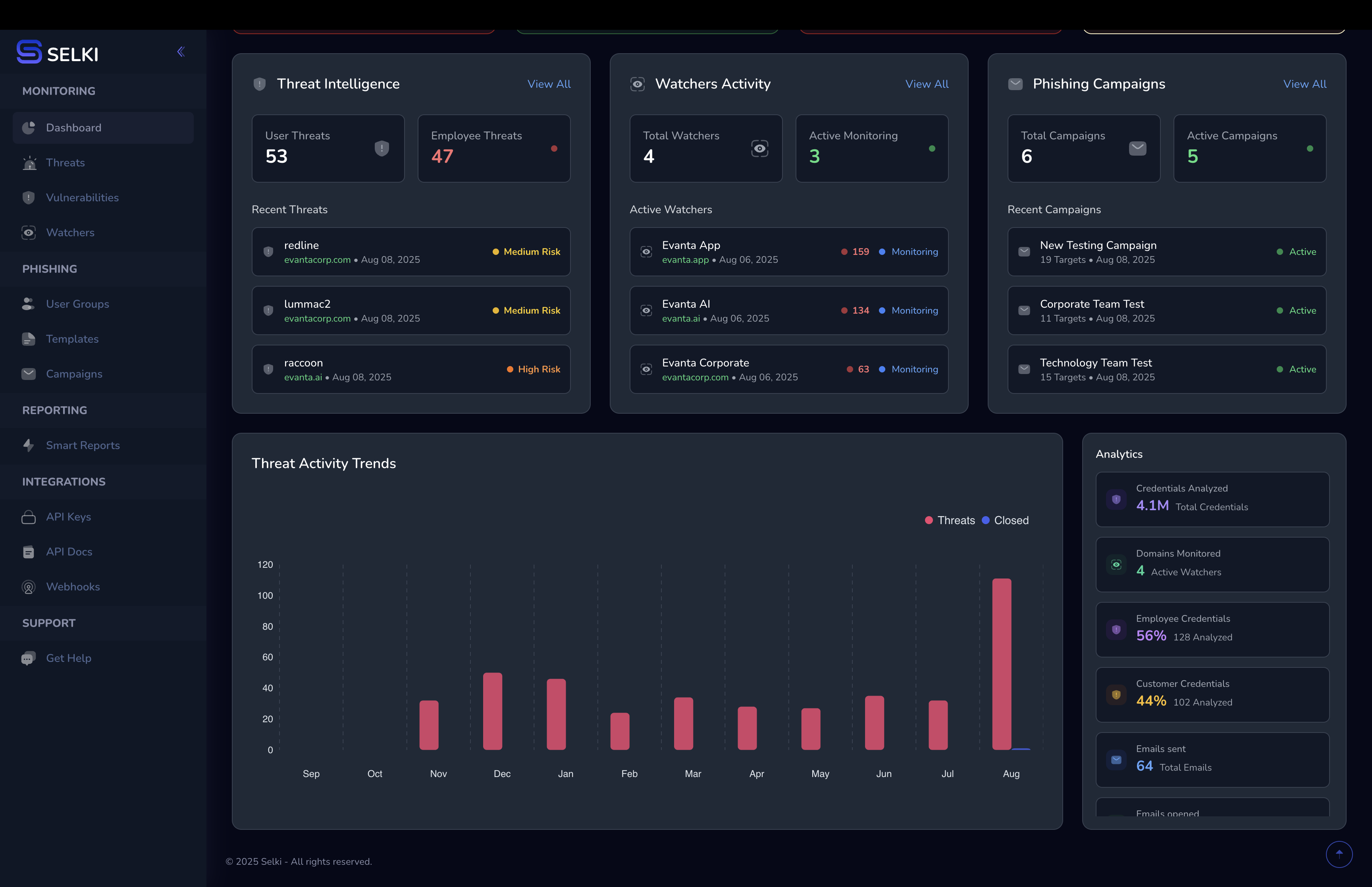
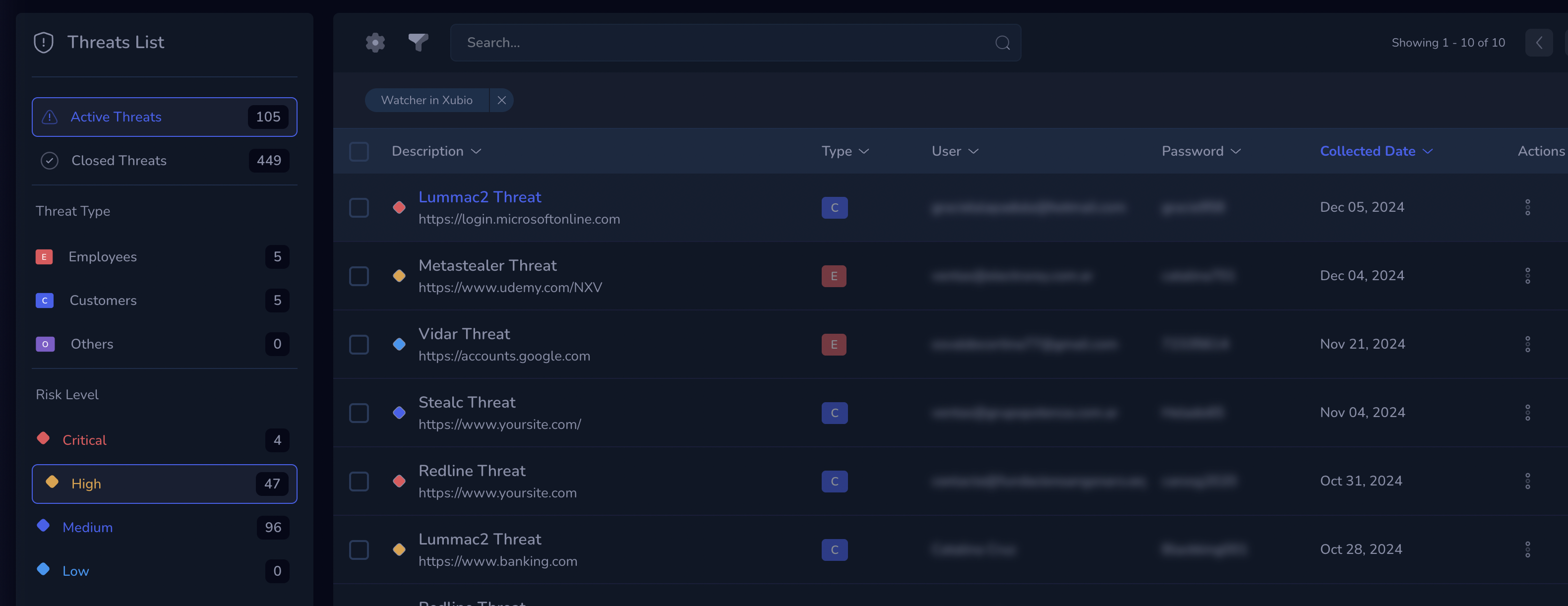
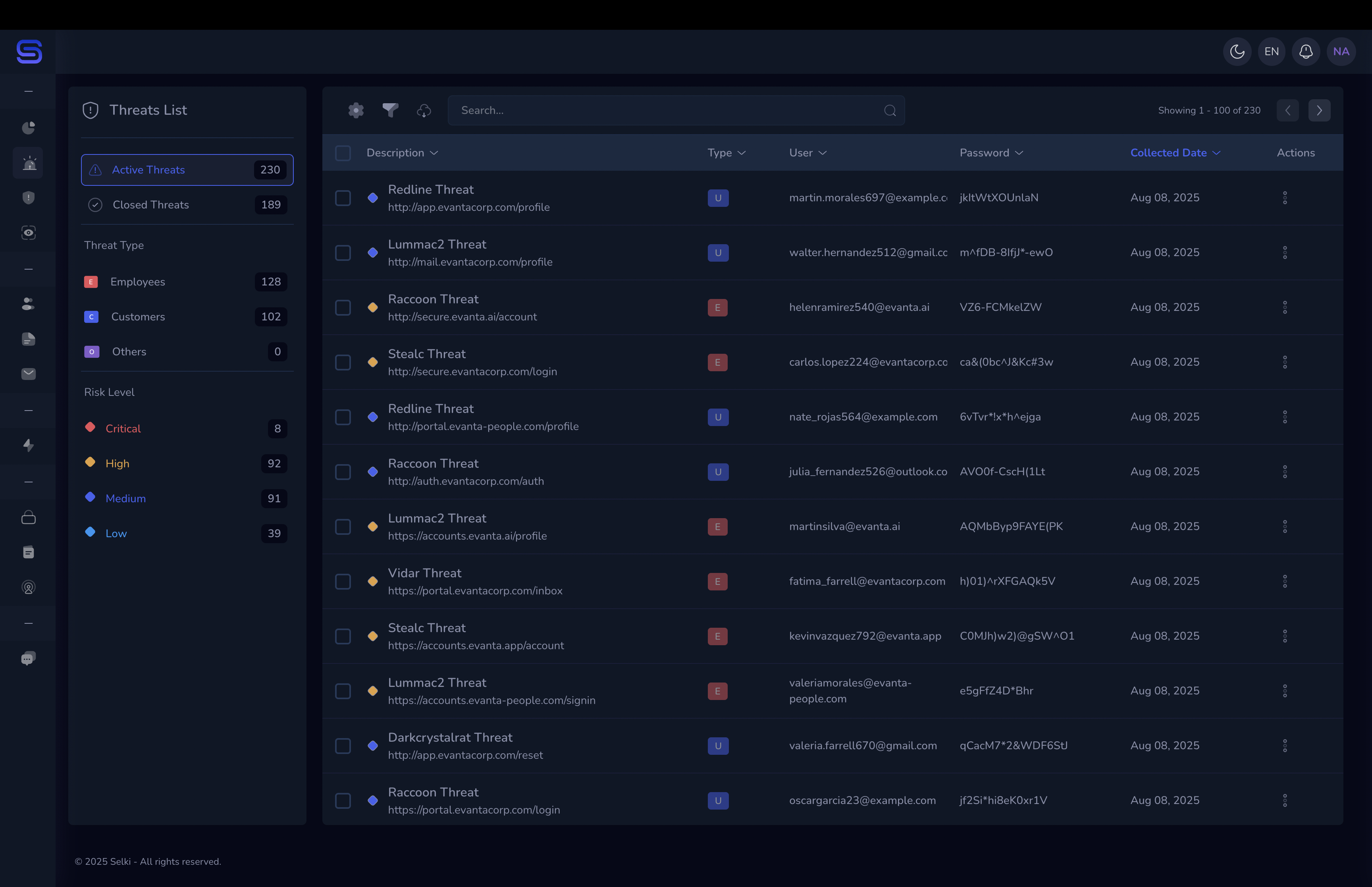
Filter by domain, campaign, user, or risk profile—see what matters most to your business.
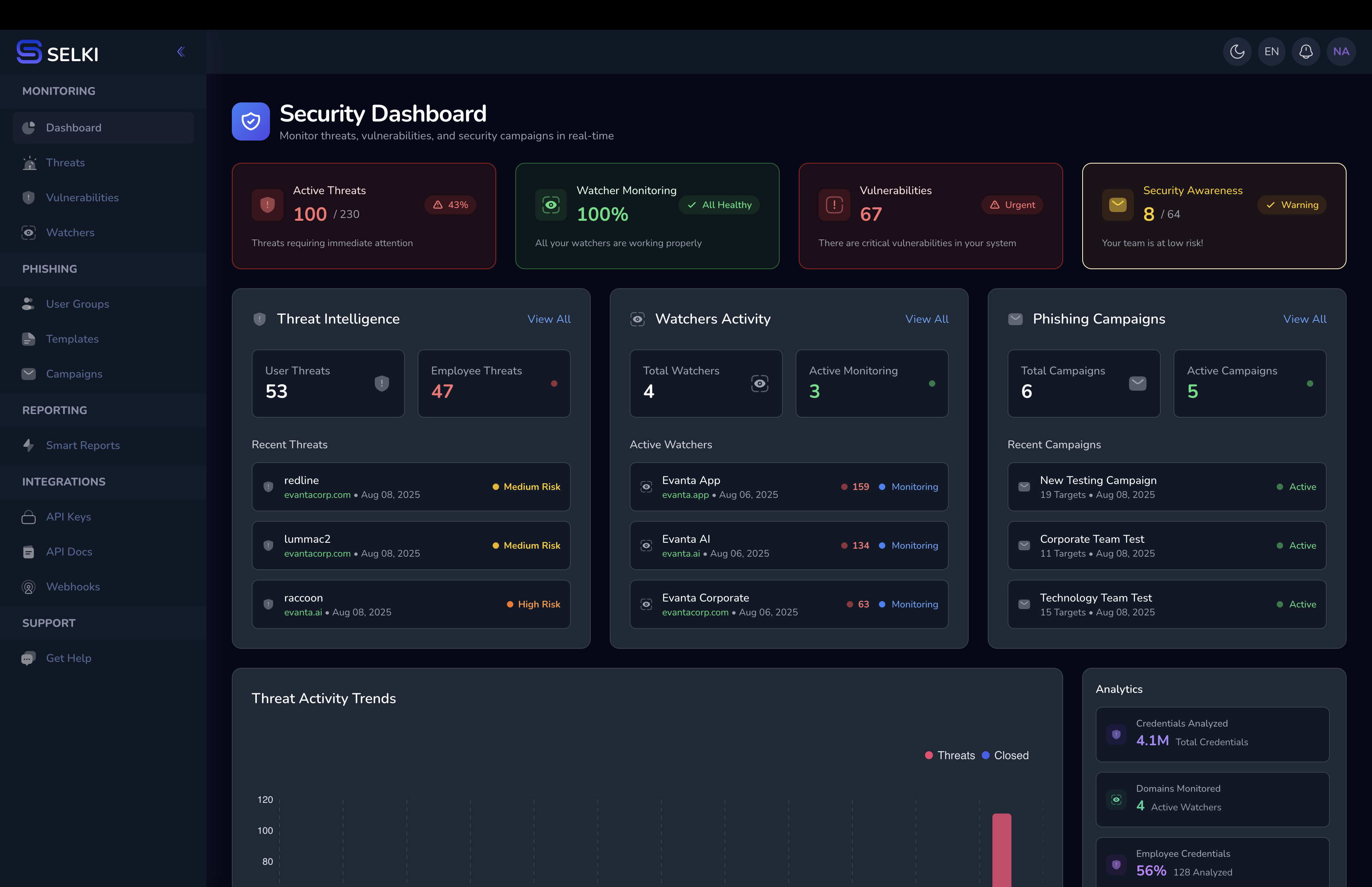
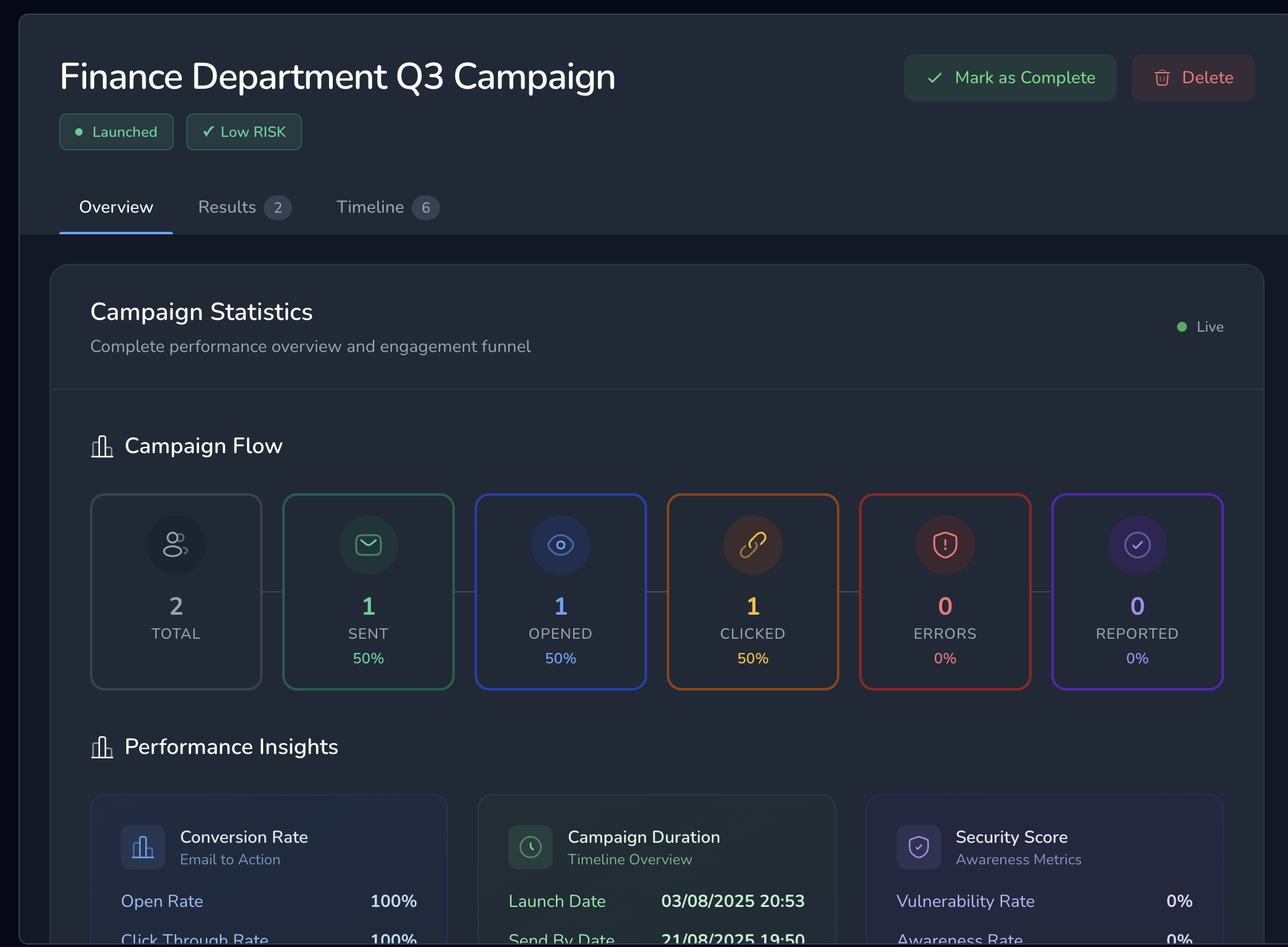
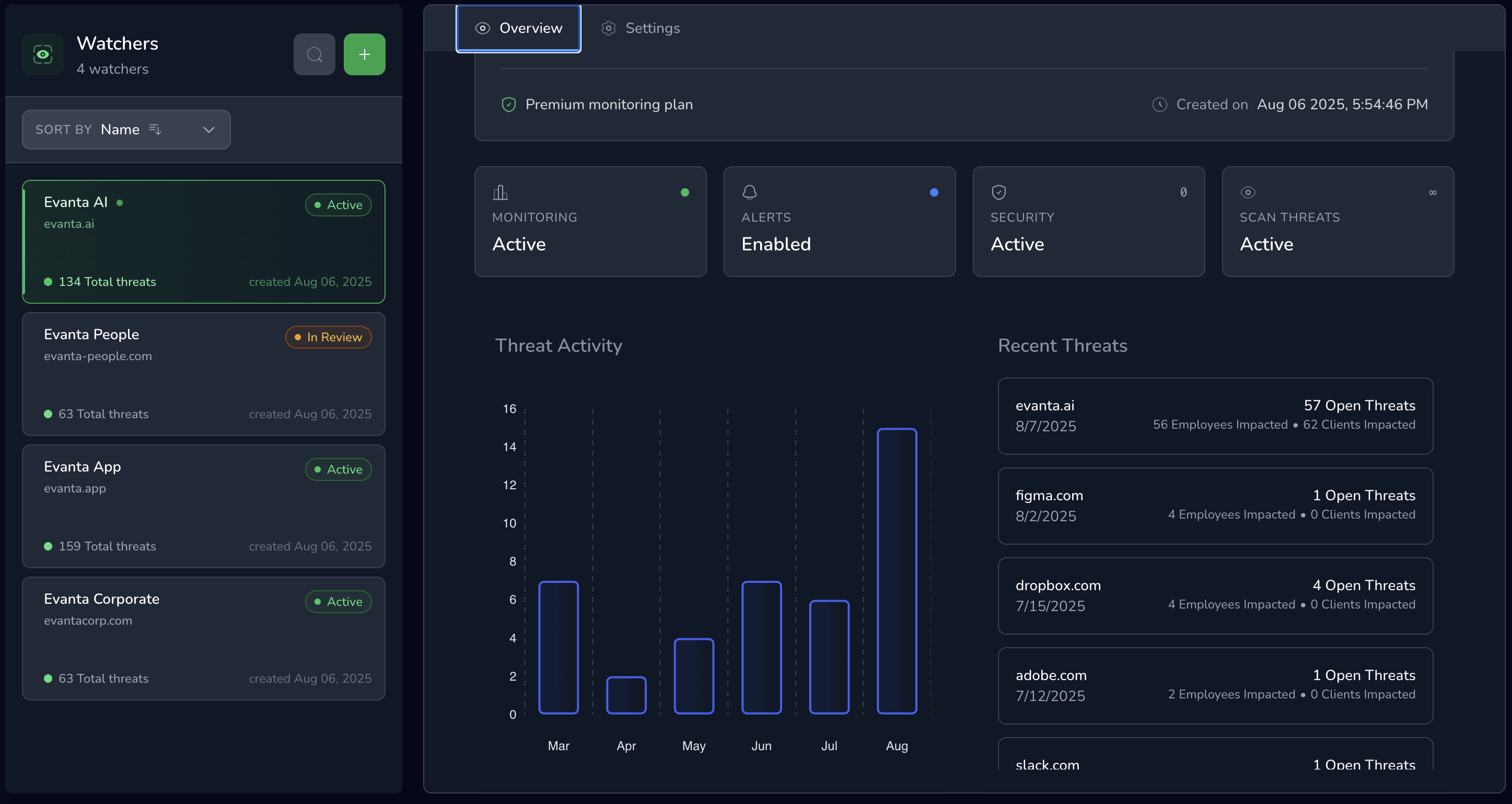
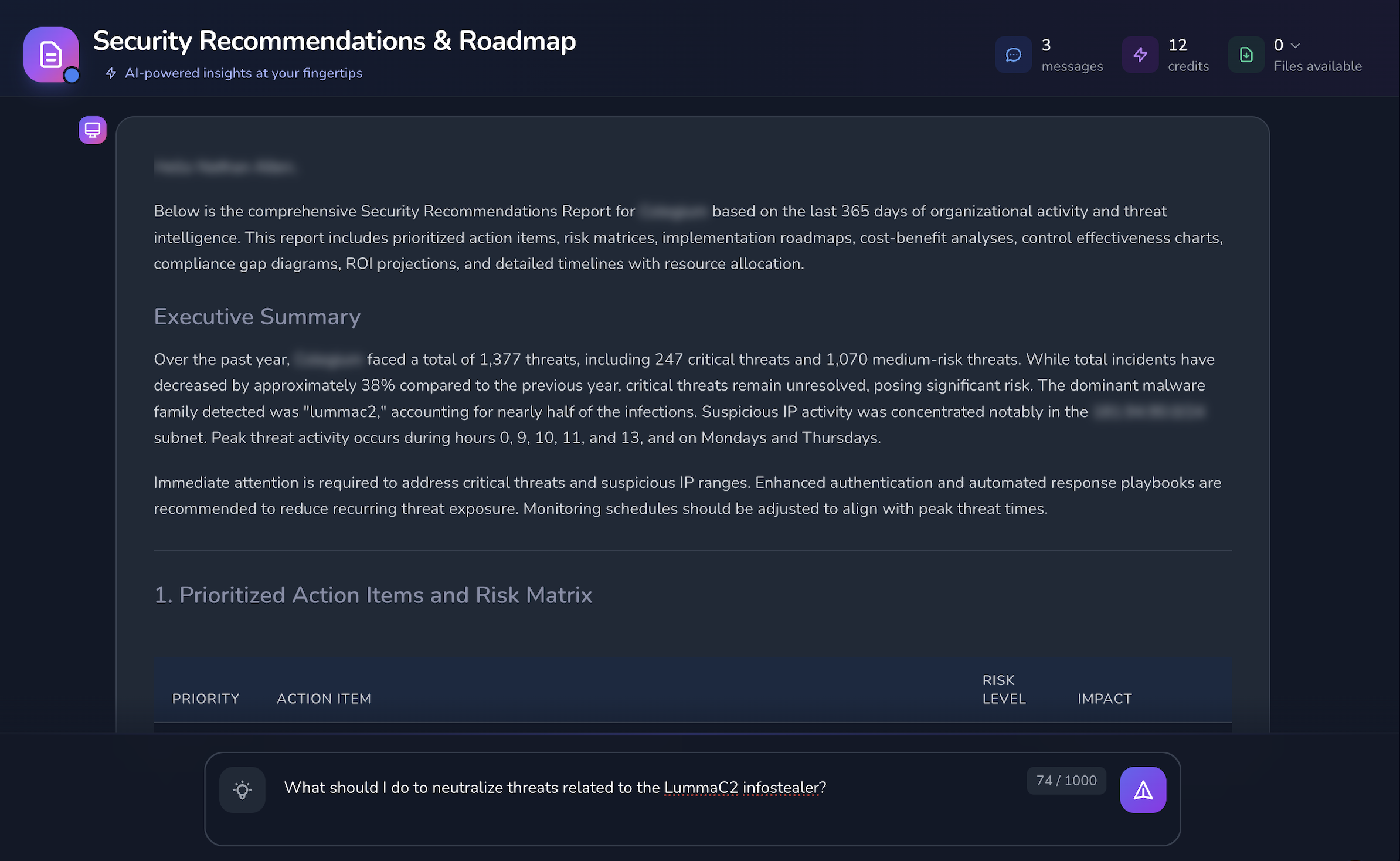
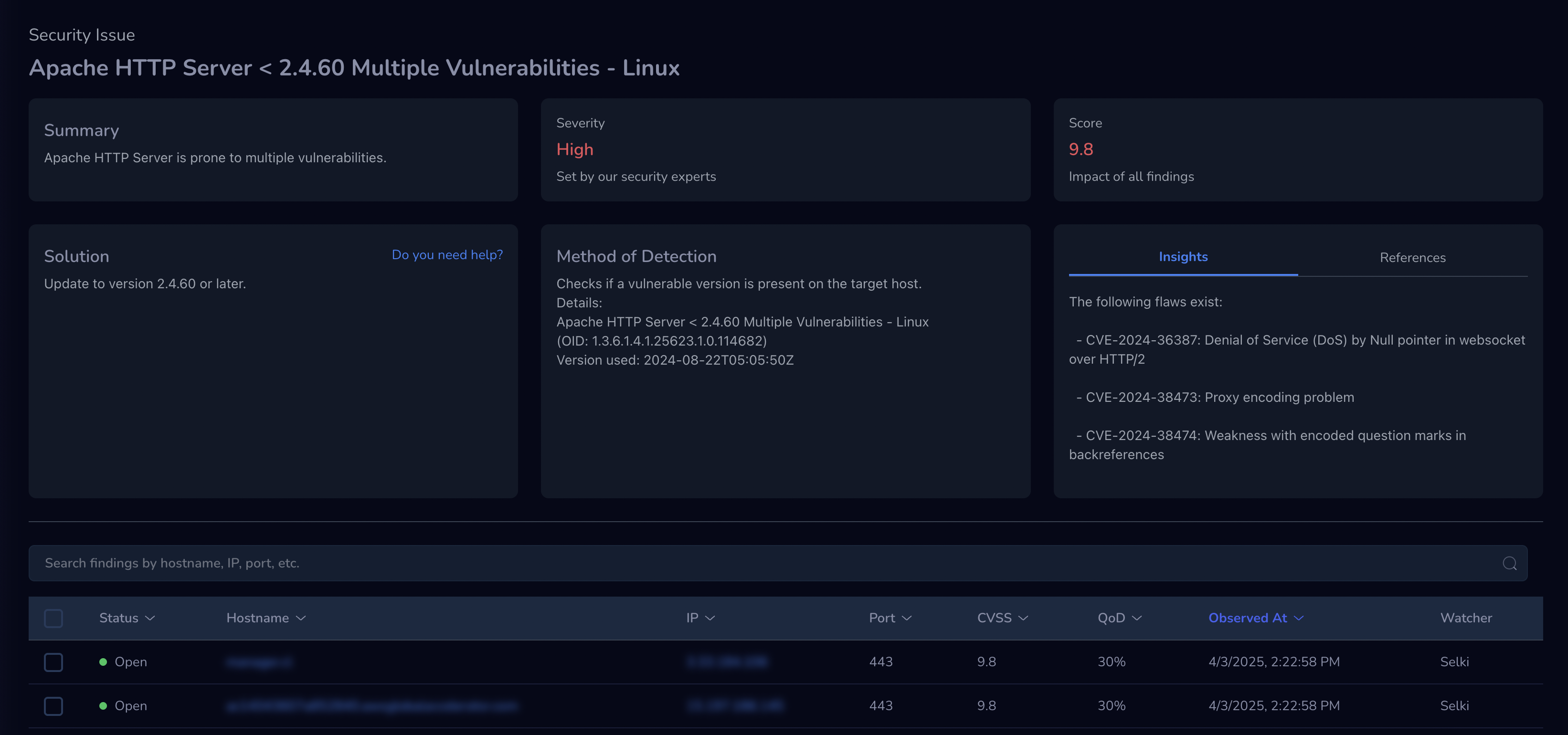
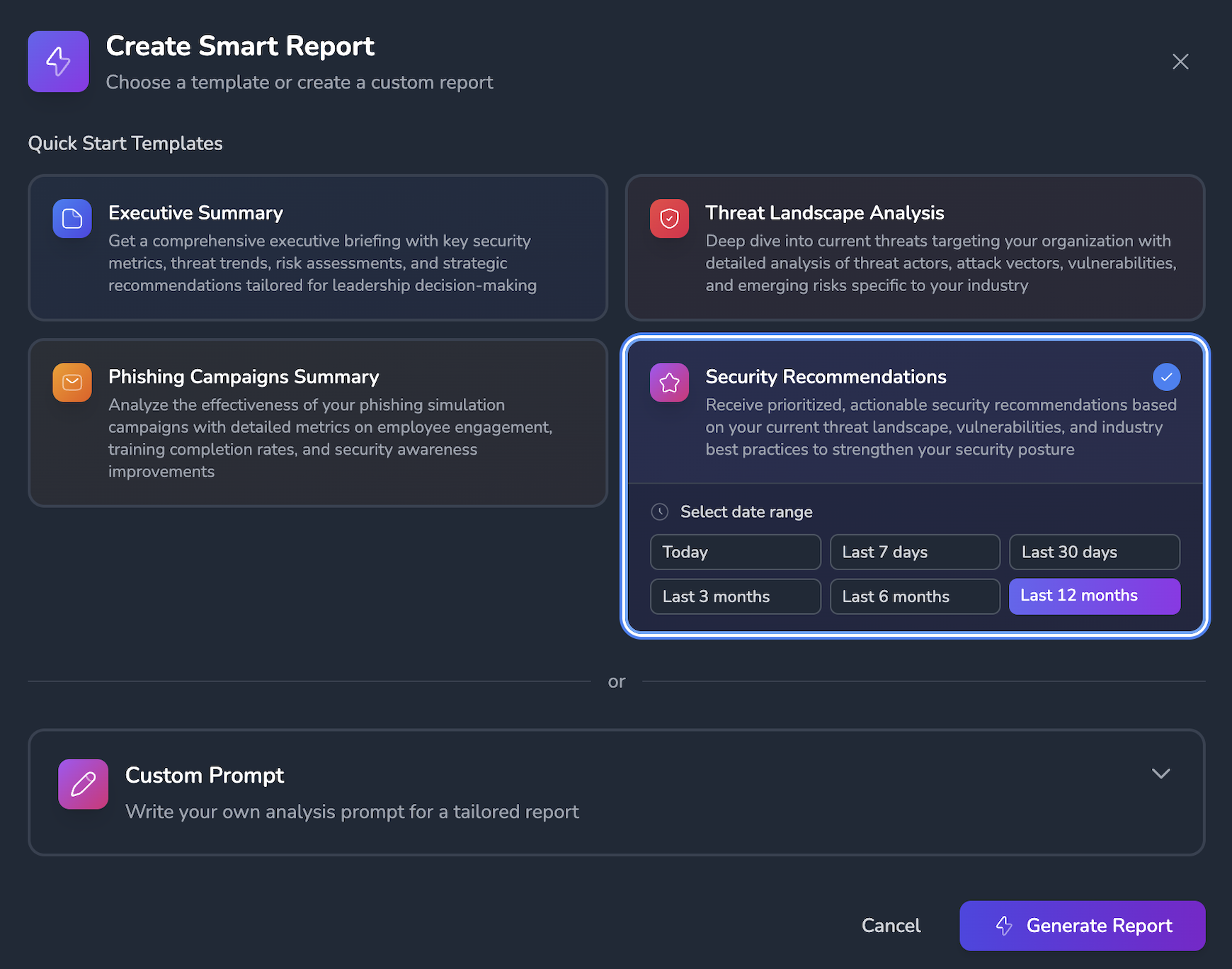
Turn security data into clear insights about your real risks.